Improve your passwords now! Understand the risks, take action and create excellent passwords

This article is general knowledge and a guide for clients. The how-to guides and policies apply to anybody who has concerns about security and password management.
If we’ve directed you to take a look at this article you may have sent us a password by email, shared your account details or even worst, another of your contractors may have shared credentials with us poorly.
We know that staying on top of this stuff is not always at the forefront of your mind, nor do you find it particularly exciting or interesting. We’ve tried out best to make it so and are 100% confident that you’ll read this and find a way to make a positive impact on the way you use, manage and share passwords and access.
Cyber Criminals: What we are up against.
How are passwords cracked and accounts hacked?

Brute Force
A brute force attack is as it sounds. Once one computer can attach itself to another ie via a login screen, an API or other method it can (in theory) keep attacking the login area and trying multiple usernames and passwords over and over again.
In reality, there are rate limiters in place, that all too familiar “too many failed login attempts, you must wait 5 minutes” message but that isn’t always true.
Your average medium-powered business computer is capable of running 40 Billion operations per second. That’s just one, one single computer capable of trying 40 Billion options a second. So let’s assume for a second there is just one computer trying to attack ours.
How long would it take to crack?
| Password Type | Password | Time for 1 computer to crack |
|---|---|---|
| A plain text password 10 characters long | osaaeitfzt | 59 minutes |
| Numbers and lowercase letters 10 characters long | 0saae1tfzt | 1 day |
| Numbers, special characters and lowercase letters 10 characters long | 0s##e1!fz! | 1 month |
| Numbers, special characters, uppercase and lowercase letters 10 characters long | 0S##e1!fZ! | 5 years |

5 years you say. Great! Nope….
This is assuming just one computer. You could go to Digital Ocean or Amazon AWS right now and buy 100 computers and have them running in 20 minutes and it would cost less to run them than buying a computer
A password that took 1821 days (5 years) with1 computer now takes 18 days.
And this is exactly how viruses are designed to work. Infecting millions of computers at a global level then turning them against systems to work as a unified code-breaking machine with trillions and trillions of processes per second.
Then there is the fact that every year computers get more powerful. Moore’s Law refers to Gordon Moore’s (CEO and Co-Founder of Intel) perception that the number of transistors on a microchip doubles every two years, though the cost of computers is halved. Moore’s Law states that we can expect the speed and capability of our computers to increase every couple of years, and we will pay less for them.
Have you been making your passwords twice as hard to crack each year?
Phishing & Spear Phishing
Unlike brute force attacks Phishing and Spear Phishing is more sneaky and tactical. Phishing attempts to get users to submit their credentials into a system that is under the attacker’s control. The most familiar of these are emails from your bank or service provider asking you to log in for a security message or urgent action.


Sometimes these emails, texts, phone calls can be more targeted (Spear Phishing). They may already know something about you or your company such as a Director’s name or employees personal email address.
A common Spear phishing tactic is to find the Managing Directors name and email then spoof the email address whilst messaging the accounts department asking them to pay somebody urgently. For this reason its important to have an internal system of approving payments.
Phishing and Spear Phishing can be easier to avoid by not sharing your credentials or trusting messages asking to enter or re-enter credentials.
If you believe it is true then go directly to the website or system in question, without following a link and when you log in you will see any actions you need to take.
Data breaches and leaks
Vigilante has records showing there have been 4,522 reported breaches with almost 4.5 billion records exposed. This means hackers have a vast library of passwords to try.
Passwords that would be secure under brute force can be hacked almost instantly and to make matters worse the passwords are usually linked to email accounts. Many people use the same passwords across their email accounts as well as their systems which means that once they are in your email they can reset all of your passwords and lock you out or gain access to anything else they can detect.
And…becase they have your email address they can utilise Spear Fishing tactics.


“Hey, Jon. The password “mrbiggles” you use to login with your account at Amazon.com with email address mrjonbiggles@email.com has expired. Click here to reset it”
They know my name, they now my password, they know my email address. It must be real!!! Wrong. You are being redirected to a fake website that is gathering more information or collecting your new password.
Passwords you should not use
These are the top 25 passwords that are used. They are the first to be tried and are cracked instantly. You should NEVER use anything on this list.
- 123456
- password
- 12345678
- qwerty
- 12345
- 123456789
- letmein
- 1234567
- football
- iloveyou
- admin
- welcome
- monkey
- login
- abc123
- starwars
- 123123
- dragon
- passw0rd
- master
- hello
- freedom
- whatever
- qazwsx
- trustno1
How to be awesome at passwords
Now we understand the types of attacks, how hackers use our information and what not to do let’s take a look at how we can secure ourselves without making life difficult.
Creating secure passwords
- We’ve seen that a 10 character password is insecure.
- We know that computers can be combined into code-breaking machines.
- We also know there are roughly 7 billion people in the world and that there are approximately 3 devices per person (Tech Crunch).
- So we need a password that if all the computers in the world combined forces to try and hack it, they couldn’t.
32 characters are the optimum
Here is a 32 character password generated by our password management tool Lastpass Z@Xv180s!xmbsAvfurcbyPr5CjGF%Q
To crack this password will take 2,000,000,000,000,000,000,000,000,000,000,000,000,000,000 years
If everyone on the planet had as many computers equivalent to the number of grains of sand on earth, it would still take 300 million years to crack
*Z@Xv180s!xmbsAvfurcb*yPr5CjGF%Q
But what about if you don’t have a password management system that remembers complex passwords and types them for you?
*Z@Xv180s!xmbsAvfurcb*yPr5CjGF%Qmay be practically impossible to be cracked, however, it is also practically impossible to be remembered
Password length is the key
tkccslgf– 5 secondstkccslgftkccslgf– 35,000 yearstkccslgftkccslgftkccslgftkccslgf– 2 octillion years
We can, therefore, put four/five random words together and make a long and easy(er) to remember password. This is possible due to the high number of words in English that are in common usage. Lets use these four words
- Fancy
- Librarian
- Politician
- hesitation
Fancylibrarianpoliticianhesitation
This easy to remember password would take 1,000,000,000,000,000,000,000,000,000,000 years to crack by a single computer and 2.5 hours if every person on the planet had as many computers as there are grains of sand.
Tools for managing your passwords
Our favourite tool for managing passwords is Lastpass. We can create a folder per client or project and share it through our business with control over who can use, see and edit passwords. Each team member also has a personal account for storing credentials for them.
It’s easy to use on mobile devices as well will autocomplete from the keyboard and also Mac and PC apps available.
3 Password manager recommendations:
Everyday password how-to
How to give an agency/freelancer access to your Magento Store
You will most likely have user roles set up internally for your business. When working with agencies we find it useful to have a User Role per Agency.
Total Time: 5 minutes
- Create a new Magento User Role
%22%20transform%3D%22matrix(3.75%200%200%203.75%201.9%201.9)%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20fill%3D%22%23727272%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(-7.26878%20189.71467%20-27.58654%20-1.05696%200%2096.4)%22%2F%3E%3Cpath%20fill%3D%22%23fff%22%20d%3D%22M256%20136l-1-152L21%2058z%22%2F%3E%3Cellipse%20fill%3D%22%23cdcdcd%22%20cx%3D%2232%22%20cy%3D%2257%22%20rx%3D%2220%22%20ry%3D%22255%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20cx%3D%22142%22%20cy%3D%2275%22%20rx%3D%2292%22%20ry%3D%22210%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
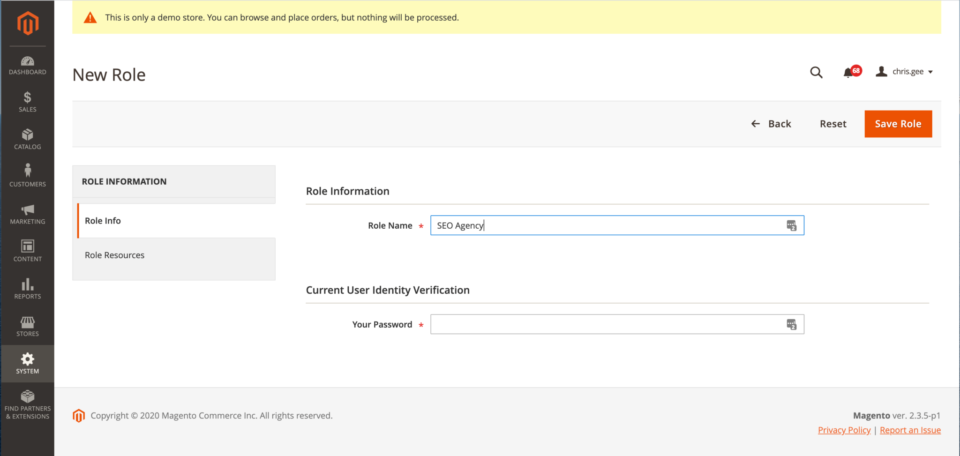
Go to System > Permissions > User Roles
Create a new role such as SEO Agency, PPC Agency, Content Agency - Give resources to the new user role
%22%20transform%3D%22matrix(3.75%200%200%203.75%201.9%201.9)%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20fill%3D%22%23767676%22%20cy%3D%2269%22%20rx%3D%2226%22%20ry%3D%22255%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(-112.40503%20-15.59749%2021.41465%20-154.32704%20159.2%2069.6)%22%2F%3E%3Cellipse%20fill%3D%22%23cecece%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22rotate(-179.3%2014.3%2031)%20scale(17.71106%20152.16165)%22%2F%3E%3Cellipse%20fill%3D%22%238c8c8c%22%20cx%3D%223%22%20cy%3D%2245%22%20rx%3D%226%22%20ry%3D%22194%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
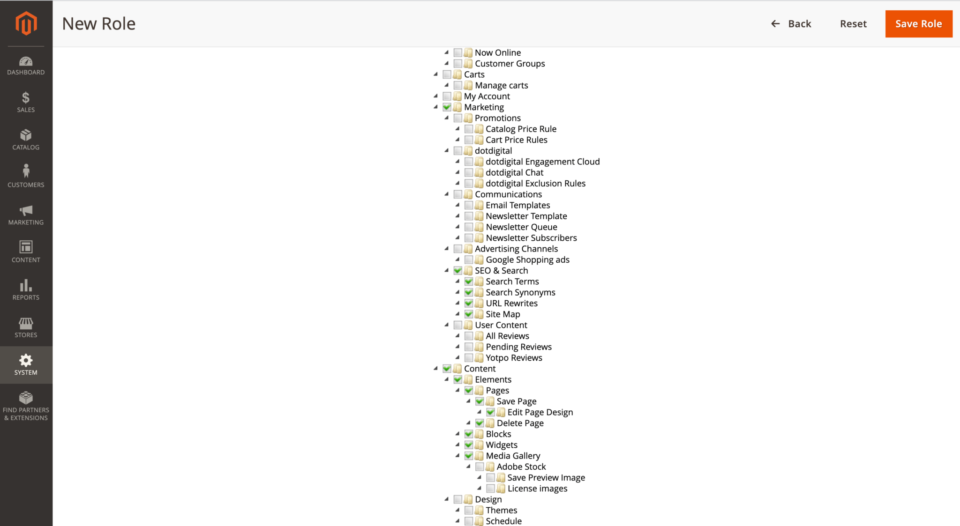
Under Role Resources choose the functions this agency will be allowed to perform by ticking the boxes.
Make sure “Custom” is selected if you don’t see any checkboxes.
- Add users to your new agency user role
%22%20transform%3D%22matrix(3.75%200%200%203.75%201.9%201.9)%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20fill%3D%22%23fff%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(121.69073%20-224.09009%2039.68153%2021.5488%2021%2045.7)%22%2F%3E%3Cellipse%20fill%3D%22%23d5d5d5%22%20cx%3D%22183%22%20cy%3D%2255%22%20rx%3D%22123%22%20ry%3D%2235%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20cx%3D%22112%22%20cy%3D%2210%22%20rx%3D%2298%22%20ry%3D%2214%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20cx%3D%2230%22%20cy%3D%2232%22%20rx%3D%2234%22%20ry%3D%22223%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
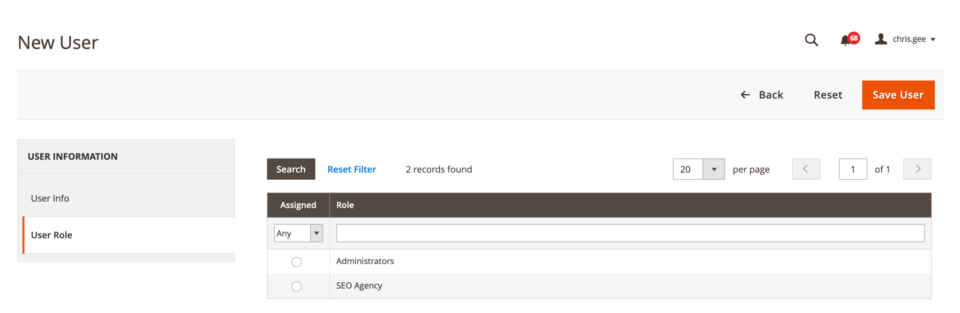
Go to System > Permissions > All Users and Add New User
When you create their password create a strong 32 character password. At this moment it really doesn’t matter what the password is. You will not be sending it to the user.
(If you are using TwoFactorAuthenication this process might look a little different but the sentiment is the same.)
Once you have completed the user’s account details you can select the User Role tab and add them to the agency user role you have created.
- Give Magento admin access to the new user


This is the important part. A password is only as secure as a secret. Sending an email to the new user with their password gives away their email address and password to the would-be cyber-criminal.
The best way for the new agency user to access the account is to set their own password via the password reset link.Email your new user and let them know an account has been created for them, and they must now reset their password.
See below for an email template
This process can be used for pretty much any website CMS. Setting a super-secure password then redirecting your user to set there own via the Forgot Password link is much safer than sending people a password.
Hi [NAME]
I have created an account for you here. If you haven’t already received an auto-generated email from our website you can go to this link [YOUR-MAGENTO-ADMIN-URL] and set your password by clicking “Forgot your password”
You’ll receive an email to reset your password and get access to the admin of the site.
There should be little or no need to share details with us. An account should be made specifically for each user at Rixxo.
Where possible instead of sharing password details with us either;
- Create an account of our own
- Reset our existing account password
Telephone
Sometimes the easiest way to get secure details across is by phone. It’s always best to double-check the details whilst on the call. Call us.
SMS or Whatsapp
- Email the username
- SMS or Whatsapp the Password to your account manager.
Confidential Email (GSuite)
- Put the details into the email
- Send the email in confidential mode requiring the user to get a mobile unlock code
- Send the SMS passcode to your account manager
